
Key Highlights
-
21 hours of video lectures
-
Study on mobile or laptop
-
Lifetime LMS acces
-
Live or recorded sessions
-
Certificate of completion
-
Industrial projects
-
Internship opportunities
About Course
This course covers the fundamental concepts underlying the construction of secure systems, from the hardware to the software to the human-computer interface, with the use of cryptography to secure interactions. These concepts are illustrated with examples drawn from modern practice and augmented with hands-on exercises involving relevant tools and techniques. Successful participants will develop a way of thinking that is security-oriented, better understanding how to think about adversaries and how to build systems that defend against them. This course provides learners with a baseline understanding of common cyber security threats, vulnerabilities, and risks.
What Will You Learn?
- Understand the basic concepts and terminologies used in the information and cyber security fields.
- Understand how hackers actually hack.
- You will be trained in all the ways hackers can socially engineer you, through email, text, calls, browsing, files, mobile phones, connected home devices, etc.
- You will stop successful social engineering attacks, by spotting red flags in phishing emails, text messages and phone calls.
- You will be shown proven and effective cyber security software to keep your systems private and secure.
- You will learn cyber security awareness and online self defence to protect yourself?
- Intern with us on live projects.
- Develop an insight of a Artificial intelligence queer
- Know which algorithm/ model to implement at different problem statements
Course Content – Cyber Security
- What is Hacking?
- Hacker Classes
- Ethical Hacking
- Threat, Vulnerability and Risk
- Importance of InfoSec
- CIA Triad
- Security, Functionality and Usability
- Hacking Methodologies
- Foot printing
- Procedures in Reconnaissance
- Data Retrieval Scope
- Foot printing Methods
- Reconnaissance Methods
- Active and Passive Reconnaissance
- Why scanning?
- Objectives of Network Scanning
- Communication Flags
- Types of Scan
- Identifying results from Scans
- Enumeration
- Information Enumerated
- Types of Enumeration
- Enumeration Tools
- Gaining Access
- Maintaining Access
- Clearing Tracks
- Hacking Stages
- Penetration Testing
- System Hacking steps
- Password Complexity
- Password Cracking Techniques
- Defence against Password Attacks
- Sniffing
- Types of Sniffing Attacks
- ARP Poisoning
- MAC Flooding
- DNS poisoning
- DHCP Attack
- Sniffing Tools
- Defence against Sniffing Attacks
- Trojan
- Communication Channels
- What do hackers look for?
- Goals of Trojan
- Types of Trojans
- Indication of a Trojan Attack
- Trojan Tools
- Computer Virus
- Computer Worm
- How Viruses work?
- Types of Viruses
- Counter Measures for Viruses and Worms
- DOS/DDOS Attack
- How does DOS work?
- Symptoms of DOS
- DOS Techniques
- DOS Counter Measures
- Session Hijacking
- XSS Attack
- Steps involved
- Session Hijacking Tools
- Prevention against Session Hijacking
- How web applications work
- SQL Injection Attack
- Wireless networks
- WEP
- WPA
- Wireless Hacking Methodologies
- IDS/IPS
- Firewalls
- Vulnerability Assessment
- Vulnerability Management Process
- Phases of Vulnerability Management
- Report Writing
- Constituents of a Report
Learning Plans
Check the pricing plans below that suits the best of your requirements.
Self Learning
₹ 4,600
₹5,900
Save up to 30%
- Recorded video lectures
- Industrial projects
- Certifications
- Live sessions
- Direct mentoring
- Doubt clearing sessions
- Aptitude grooming
- Personality development
- Group discussions
- Resume building
- Placement assistance
Mentor Learning
₹ 7,100
₹9,200
Save up to 30%
- Live sessions
- Recorded video lectures
- Direct mentoring
- Doubt clearing sessions
- Industrial projects
- Certifications
- Aptitude grooming
- Personality development
- Group discussions
- Resume building
- Placement assistance
Professional
₹11,800
₹15,300
Save up to 30%
- Live sessions
- Recorded video lectures
- Direct mentoring
- Doubt clearing sessions
- Industrial projects
- Certifications
- Aptitude grooming
- Personality development
- Group discussions
- Resume building
- Placement assistance
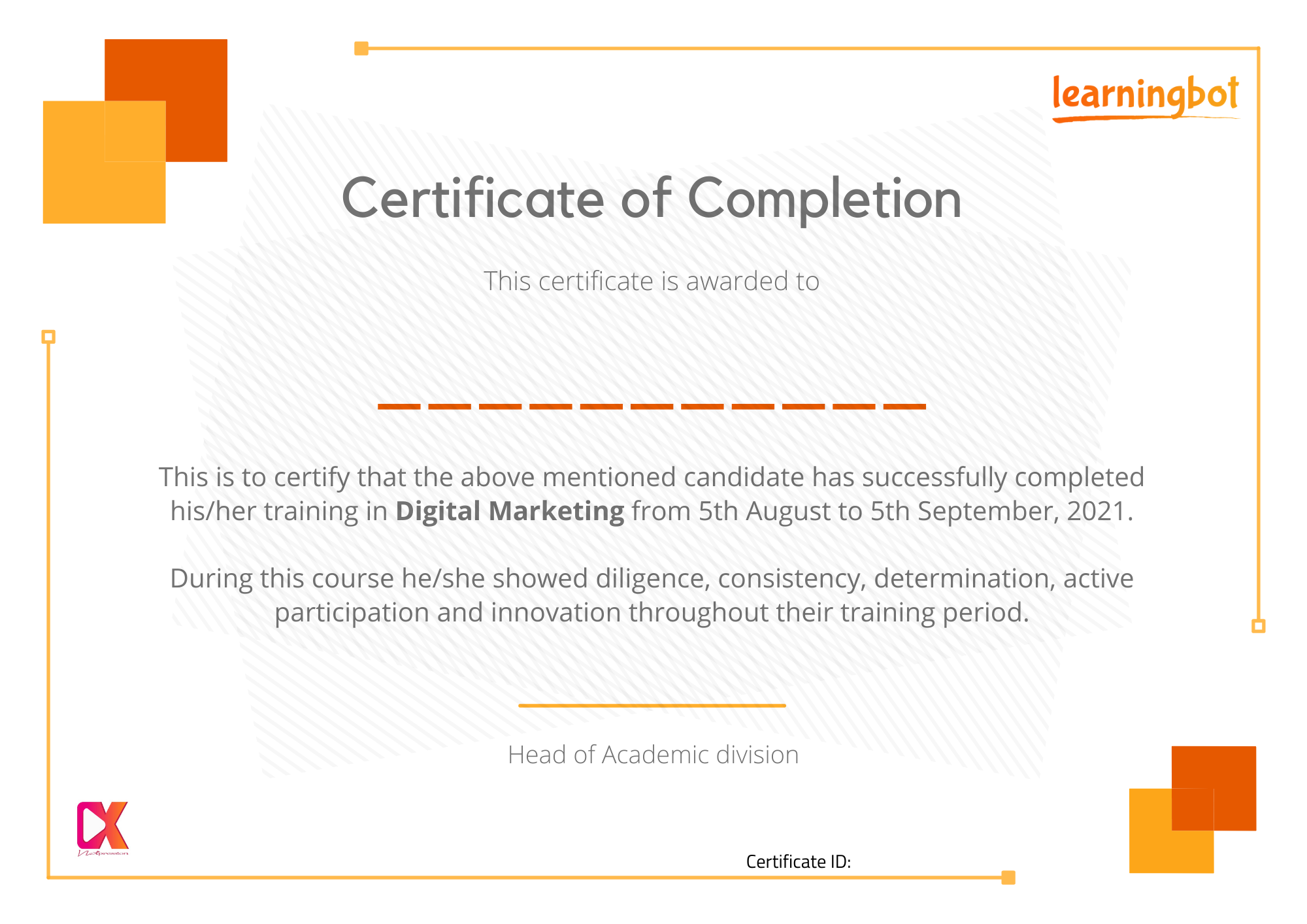
Certification
For your dedication and commendable efforts to learning, for completion of the training as well as the projects accurately and within the timelines given, you earn industry-recognized certifications.
On successful completion of your program, you are eligible to receive a certificate of completion from LearningBot
By taking a Learning program with LearningBot and completing your program, you get your certification which has validity of a lifetime.
After completion of your program of entire training module and assessments, you are eligible to obtain your certificate from LearningBot.
Testimonials



Frequently Asked Questions
As a user, you can avail a the payment mode of your choice. The available modes are: UPI, debit/credit card, No cost EMI, Netbanking/Mobile banking.
When enrolling into LearningBot’s training programs, you are associated with us for a duration of 2 months. Where as, with LearningBot’s Professional programs, you are associated with us for a duration of 3 months.
At LearningBot, you are mentored by industry experts who have been/are working in the industry for a decent time and have a strong grasp in their domain of expertise.
With No cost EMI as a mode of payment, you can easily avail the same if you qualify a basic eligibility criteria.